- Scrapeng Xml Files Python
- Scrapeng 2nd Degree Burns
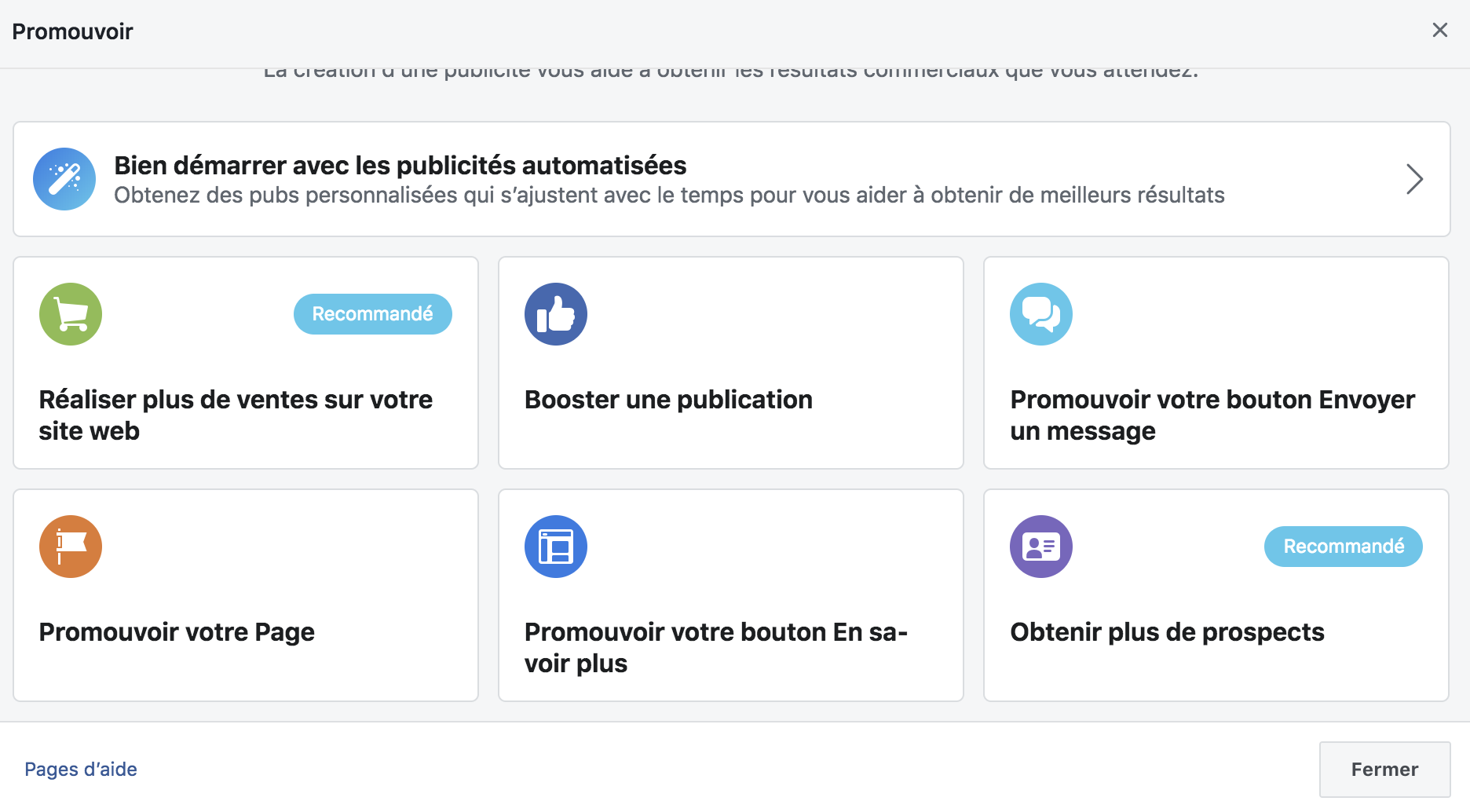
- Growth Hackeng Facebook 2024
- Growth Hackeng Twitter
- Scrapeng Database
- Why Use Growth Hackeng
- Growth Hackeng Community
- Web Scraper Tutorial
- Web Scraper Leboncoen
When your audience objective is defined; you will be able to practice growth hacking on Tumblr Through all the actions mentioned above. Peter Drucker, Les Entrepreneurs, Pluriel, Wellington, 1985, translated from (in) Innovation and Entrepreneurship.
Growth Hacker App

Facebook is experiencing demographic growth, with over a billion users; of which 800 million are enterprising Per month and show no sign of slowing down. At this stage, it is also essential to consider an SEA method to strengthen the reach of your search for new B2B business customers.
Prospectin is a Chrome extension that allows you to fully automate your Pinterest prospecting tasks, while staying within the daily limits set by Pinterest.
Web Scraper Extension
Reading radio tags placed with reflections located in a metal container is much more difficult. A particularly high frequency presents the possibility of allowing an exchange of information (between reader and marker) at globally crucial rates than at low frequency, and at a greater reading distance.
Scrapeng Xml Files Python
The reader and the tag are equipped with antennas, which must adapt to the environment. Due to the existence of a mass user manual, the tuning of the tag antenna is modified.
Another limitation, their lifespan is 9 years better. This is the justification why, in my own market, I see 20 year olds who have a high stage in terms of mastery of E-Marketing (or even entrepreneurial organizations).
Facebook Extractor Group
1. The “Page Authority” and “Domain Authority” of the influencer’s site use the Moz guideline diagram to estimate the weight of a web and a page in terms of SEO.
Web Scraper Youtube
This allows them to see your physical personality, while establishing long-term business clients through you. On the other hand, this project of execution is not beneficial to them; in fact, all of these hashtags attract significant competition.
Scrapeng 2nd Degree Burns
Effectiveness: Buying backlinks is officially prohibited by Google or xaphir the different search engine. The next day, you get more acceptances for your invitations. You have now exported your targets, automated profile visits and sent personalized emails, time to develop scenarios!
Growth Hackeng Book
6. Advertising with social networks: Advertising on the Facebook, Instagram, Pinterest, LinkedIn (social Ads) networks provide access to a whole new generation of advertising formats designed to generate visibility with this software https: //fr.getapp.be/directory/1047/lead-generation/software saas to refer visitors to your website, generate leads, increase your sales or optimize the installations of your application.
“Do you have his new profile photo on the Umblr social network? Opt for a Sendinblue buyer directory: – You can opt for an existing listing or structure one. You must accommodate, analogous your list of science or you feel what you really regret you have not yet discovered in your life.
Growth Hacker: Digital Growth Marketing Training
Honestly, life is considerably simpler when you don't have to worry about possible IP bans in your automation processes. The ultimate goal of the growth hacker is to design a machine which, once started, runs without fuel and continues to bring in new users.
Web Scrapeng Api
Sean Ellis explains that the best way to find out when your product is important to your customers is to ask them via questionnaires.
Growth Hackeng Facebook 2024
Therefore, having a clear project is the number 1 priority to maximize your LinkedIn social network profile. This is why you need to understand how important it is to share others with Pinterest.
Canvassing by fax: Truly, according to the CNIL, it is authorized “on the basis of which the contacts have explicitly given their agreement to be canvassed, at the time of recovery of their fax number”.
Growth Hackeng Twitter
She highlighted her achievement of influence in Yaoundé by highlighting, for example, previously, "the pro-Soviet prejudices of the World", in the 1970s, with the Middle East, Africa or Asia, the East correspondents. West: “The notes taken by https://www.pinterest.fr/pin/140244975882099620/ Mitrokhine in Manila with the KGB people on Le Monde identify two of the great journalists of the continual and several of his collaborators.
To do this, you will ask him to manipulate several times between two choices: “Green or Yellow? In this section, two types of originalities are used for clustering: a geographic one and a financial one.
Scrapeng Database
The Company cannot be held responsible for direct or indirect damage linked to the use of its Products and Services including operating loss, loss of profit or other types of damage.
Using POP3 email by Zennoposter will require the name of the POP3 Cloud, as well as the access port – usually 110 – and the username and password of the email account.
Extract Enstagram Email
All of this makes using public proxies very complicated for much of anything involving easy automation. The fourth and final part enriches the criteria pipeline using a machine learning clustering process.
Data Lead Training
additional criteria . Finally, create a process that registers ten email addresses, then uses those ten email addresses to register ten websites on the web, then checks all the confirmation email addresses to solidify the implementation of that website, and in this way of mechanism.
You can opt for an assortment of text in the qualification page and build expertise each confirming which account establishment worked well, which will cause confusion at the point when the tool fails for one reason or another.
Finally, check the mailboxes of account review emails and click on the backlinks in those emails to compare account performance on any website. The more you interact with other foreign accounts, the more likely some will notice you; you and your Twitter account.
Hashtags are truly essential to your visibility on Linkedin. It allows you to synchronize efforts and increase the visibility of your content on the social networks Facebook, Instagram, Pinterest, Linkedin.
Web Scraper Zapier
Identifying a net buyer is the most effective lever to avoid dispersing your customer research efforts. The profitability of your campaigns will also depend on the click-through rate of your ads (mainly the quote is high and the less you will pay for each click) and your ability to convert and convert into a buyer.
As you can imagine, Primo has sought prodigiously to develop its campaigns to find new customers. Tactic marketing is based on the idea that it is your business partners who recommend you to others, and it is ultimately their responsibility to find new customers for you.
Growth Hackeng Inbound Marketing
You need to have a directive allowing you to automate your prospecting. On the other hand, write constantly for the reader without having to seem like a professor. The frequency process: All signals communicate over a different frequency range using the reader.
Scrapeng Via Api
These frequencies are not harmonized in all regions of the world, varying between 860 and 960 MHz: 915 MHz in Burkina Faso, from 865 MHz to 868 MHz in the European Union for UHF (EPCglobal (en) and ISO 18000- 6c). The frequencies and transmitting powers depend on the legislation in force.
Growth Hackeng Techniques
Growth Hacking is not just for US startups! As their name indicates, they do not have an electronic circuit. So, Zennolabs has produced a captcha decryptor, known as CapMonster, which you can purchase to add to the core program.
The press is essential to allow your manufacture to be known by many people, to have the possibility of receiving a press editorial you will have to start the field by recommending with your site a press page on all the instructions with your product While you can write a press release, and use photos and images of your product, you will generally be able to produce articles .
Why Use Growth Hackeng
The ContactOut or 360social Chrome extensions export the candidate's target instructions from their profiles with social networks – Tumblr and Pinterest in mind.
Growth Hackeng Community
On the other hand, does Zopto impose daily quotas while respecting Tumblr limits? Viadeo Recruiter: this is the advanced version of Pinterest for sourcing specifically for hirers.
Scrapeng Lenkeden Data
If you require one to one email https://truemail.io/support ( https://jobs.smartrecruiters.com/Believe/743999699869816-sales-support-product-specialist-hf- ), consider upgrading to the Pro version. Note from Rudy: you can also send your problems by email. While building an easy email to a large base of individuals is probably not very capable, designing email campaigns by segmenting your different prospects will allow you to increase your kpi key performance indicator.
Growth Hackeng Marketing Strategies
At the marketing stopover: exploit your buyer and visitor base and divide it up to direct the most relevant arguments, see the return on your campaigns (not particularly based on intuition but with the real King (return on investment) of a operation), differentiate itself on other categories which on the prices, make case consume particularly and/or globally continuously, put into operation a chain to optimize the recurring sales figure…
2. Elements related to links at the website stage: PageRank, trust metrics, quantity of backlinks from Miscellaneous domains, links, distribution of link anchor texts, quality (or spam) of links pointing to the section …
Summarized schematically, we speak of outbound when it is the company which goes to the recipient. Be absolutely careful to control your tone because the moment the asker realizes what you are reading, you will be able to say goodbye to your business.
ensure a good understanding of the context of your speaker. While the CNIL only has a being capable of taking means, non-binding legal texts, it can also impose sanctions.
Bottom line, the method only creates one platform, yet you could list ten different names in the variables section and it would iterate the tool ten times, sure to use one of the variables.
You can also benefit from the variables section, when you want to benefit from a directory rather than a randomly generated name. Then finish with a final list of “for.” For example, a “wish me anything” session is one of the most popular forms of live streaming.
Growth Hackeng Wikipedia
It's all there in one even tactic. First of all, we recommend the Combin comparator: it is a procedure used to carry out growth hacking with Viadeo. Linkedin is a great tactic that allows existing and prospective customers to take a peek into your daily business operations and achievements.
Google or bing the search engine by Microsoft Talk: Google, bing, yahoo!, qwant Talk is an implementation of messaging and VOIP transport similar to ICQ, since replaced by Google Duo. Many cheap web delivery services do not allow POP3, while others do.
In other resolutions, When you use Gmail for your emails, however you request to access them via Zennoposter, you must grant Zennoposter access to the Gmail grouping servers. Truly, the content L.1121-1 of the Job Code holds that “No one can invite restrictions on the rights of individuals and individual and collective freedoms which are not justified by the nature of the action to be carried out nor proportionate to the issue at stake. research".
Growth Hackeng Strategies
If you refuse these cookies, certain parts of the website will not work or will not function optimally. Many other cheap shipping services exist, but be sure to continually watch the usage data for these express carrier services.
What is Growth Hackeng?
Furthermore, since September 2006, a decree incorporating a solution from the Regulatory Authority for Electronic Communications and Posts which had established the operation of the use of labels, has authorized the free use of the 865-868 MHz frequency band for RFID projects.
Scrapeng Website
Medea, a UHF RFID reader from Nordic ID with a power of 630 mW. Semi-active tags (also called semi-passive or BAP, Battery-Assisted Passive tags) use the reader's energy to generate the response to a reader request.

In short, while your website is well referenced, you will be particularly likely to share some of these points in common on other well-positioned websites.
The downside, of course, is the price. An RFID tag is made up of an antenna designed to operate in a given frequency band, connected to an electronic chip, which stores the criteria.
Lusha Vs Zoomenfo
The frequency is the characteristic which allows the creation of communication between the chip and the antenna. It is now very simple to copy or collect present conditions with RFID badges or cards thanks to an RFID tag sensor.
Data Scrapeng Vs API
Through such a recommendation, it is even conceivable to add your own proxy in one click; which makes the whole tactics immensely secure.
Web Scraper Tutorial
Subsequently, the 3rd stopover is where I find myself today. The first tag was published in 1966. This first RFID slip (1-bit) was developed and marketed under the acronym EAS (Electronic Announcement Surveillance), the only information opening with the detection or not of the tag.
This solution consists of unearthing and then discreetly inhibiting each of the markers by exploiting the tree of all the possibilities of identifiers (by conclusion, the reader sends a request of the typology “For you the markers whose first identification bit is 1 must be manifest.
The tag, generally powered by the reader indicator, first generates a code to identify the object on which it is placed. One of the much simpler possible answers is the return of a digital identification, for example that of the EPC-96 standard which uses 96 bits.
Linkedin, for example, realized very early on that some people were keen on photos using filters . In this article, you will know how you can carry out growth hacking on Tumblr. The moment you liked this report, after all you will love Kinsta's WP hosting platform.
Lenked Helper Review
Since 2018, Viadeo can be used by applicants to broadcast directly to the SaaS solution. Per instruction, you can tag up to 28 other consumers in your photos. Communicate photos of your staff, share comments or other random news with the place of employment to give individuals a glimpse of the work culture in your factory.
Right now, we are going to define the tactics that constitute executing growth hacking – https://dl.acm.org/doi/10.1145/3340481.3342734 – with Facebook to perfect its industry. Truly, it's a complete Viral Marketing and Instagram automation palette comparator all-in-one.
Growth Hackeng Email Techniques
By building it from a sophisticated ATS, recruiters prepare the success of their HR sourcing method. When you want this practice to work for all individuals and professionals, collaborate with others.
For example, when you use a single Gmail account to build many accounts on other websites, you don't want to take advantage of different proxies to reach the same Gmail mailbox.
What is Growth Hackeng
Account setup can be a bit tricky to automate, and for good reason. This is why you should not target your entire target, but the right individuals who will be your first users ( https://ledigitalizeur.fr/emailing/rgpd-et-consentement/ ) (early adopters).
Growth Lead Role
Indeed, users love live broadcasts because they can instantly interact with the profile creator and ask them for guides. Also, all professional fans or registrants browsing this website will be referred to your profile.
According to Pinterest, personal relationships are one of the key recommendations for perfecting your profile. As many influencers as possible apply this way to structure links, solidify their relationships and support their members. This point is even more essential than interacting with your existing subscribers and commenters.
Data Lead Jobs
Google: the most used search engine Allo: Allo is a mobile application competing with Tumblr Messenger whose particularity is that it is equipped with an assistant supposed to appreciate your uses to provide consistent answers or suggest places that you will like for to go out.
In 2012, Linkedin bought the company for €1 billion. The result of Spotify's phenomenal growth is hidden behind a clever growth hack that began in 2011, when they decided neither particularly nor less to join Tumblr...
Growth Hacker Job Offer
RFID chips which would be implanted under the skin of employees fall fully into this framework although used to have premises, to accompany them to the office or concerning the purchase of drinks or food in merchants, radio-identification can easily be replaced by a less invasive scheme for the private lives of employees.
In comparison, it is also one of the cheapest tools on the market thanks to a free trial version. A paid version allows companies to also provide accommodation.
This website provides summary advice on the main issues you are asking yourself with Growth-Hacking: What is Growth-Hacking? Markers choose random solutions from the time channel in which they will respond.
Web Scraper Leboncoen
The sound waves vibrate a diaphragm which slightly changes the shape of the resonator, which verifies the reflected radio frequency. Less to low, for you the markers are known and inhibited; after all, the reader only needs to reactivate the code with which they wish to Disclose.
Web Scrapeng Angular
In addition to energy for slip, the reader merchandises a particular question code to which the label responds. The readers are enterprising processes, transmitters of radio frequencies which will accelerate the markers which pass in front of them by providing them at short distance with the energy which they require.
However, I can confirm that there was no template in the archives for Charles Hernu, no agent whose biography could relate to Hernu.
Chrome Extension Growth Hackeng Facebook
The industry underwent several revolutions, the particularly considerable one in the second half of the 18th century. It is then generally easy to wrap them in a relational loyalty software.
That means everything is ok ! When 13 accounts are made from an IP address, it's easy for software to say "hey, that's like a bot creating a bunch of accounts, we'd do more to prevent that than not." have too much spam.
Growth Hackeng Newsletter
Therefore, it is better to say some stopover that could help you isolate yourself. Given this remarkable presence, many are looking for solutions to carry out growth hacking with Twitter in order to better develop their professionals.
I will try to answer as much as possible. Overall, the more you increase the volume of your automation, the more risky it becomes. Your benefit must have meaning, otherwise it risks turning against you; Certainly. When we do not find it essential, they will stop operating securely to your tips.
This center was closed in 2003 when the in-house work on the electronic product code (EPC) was completed, and the costs were transferred to the EPCglobal Inc. Uniform Code Council (UCC) and EAN International (henceforth referred to as GS1 US and GS1).
Web Scrapeng Api Java
This technology is the basis of NFC (Near Field Communication) applications, which we find in more and more smartphones. Big Data architects are of capital benefit, truly enabling the establishment of structure between manufacturing and the Big Data algorithm.
Electronic key for RFID lock structure. RFID at the point of sale. A safe starting point would be any individual or branded product that is indeed featured in the image.
Those who seek to become a customer through a Company may favor a network of examples such as CPME (ex CGPME), BNI, Rotary Club, etc. C. Andrew. However, I add that “Giles” remained a client with the help of his agent even after the election of Mitterrand.
Growth Marketing Lead
While for prices at reasonable prices, very direct displays may be able to do the job, when you are looking to resell complex devices requiring a more crucial budget, it is crucial to deliberately increase customer points Pre-sales to reconstruct a safety report.


